AI is not only a mean thing that will put the Ghibli studio unemployed. The proof with Microsoft Security Copilotthe AI assistant specializing in cybersecurity, which has just discovered around twenty critical vulnerabilities in the bootloaders Grub2, U-Boot and Barebox.
If you use Linux / Unix or on -board systems, this news concerns you suddenly & mldr;
These new vulnerabilities make it possible to bypass Secure Boot, to install undetectable bootkits and to remain in place after resettlement of the system. Clearly, your system can be completely compromised, even if you reinstall your bone or change hard drive.
By putting Security Copilot on the spot, Microsoft was able to combine this AI approach with conventional techniques such as static code analysis (codeql) and fuzzing (AFL ++).
As a result, around twenty vulnerabilities discovered with an estimated time saving about a week compared to what manual analysis would have taken.
For the muggles that read us, know that a bootloader is the small program that runs first when you start your computer, even before the operating system wakes up. GRUB2 is that used by default on most Linux distros as Ubuntu. As for U-Boot and Barebox, they are rather in on-board systems and connected objects.
SECURITY COPILOT identifying a vulnerability to exceed whole and suggesting a correction
The research process is quite fascinating because the AI first identified risk areas (networks, file systems, cryptographic signatures), then focused on file systems. Security Copilot thus identified five potential problems, and after manual verification, only one real usable vulnerability (an entire excess) was confirmed. From there, the AI looked for similar patterns in other files.
Is it nice no, when it works well like that?
What makes these vulnerabilities particularly dangerous is that bootloaders work without the modern protections of operating systems. No DEP, no ASLR, no protection of the battery & mldr; In addition, GRUB2 is written in C, a language without integrated memory protection, and which offers a huge attack surface with its images of images, its network support and its management of multiple file systems.
Here are the most crisp vulnerabilities among the 11 discoveries in Grub2:
- CVE-2025-0678 : Entire of whole in reading Squash4 files (the most critical, CVSS 7.8 score)
- CVE-2024-56737 : Tampon surpassing in the assembly of HFS file systems
- CVE-2024-56738 : Attack by auxiliary canal in the cryptographic comparison function (not constant in time)
- CVE-2025-1118 : The DUMP command allows arbitrary reading of memory
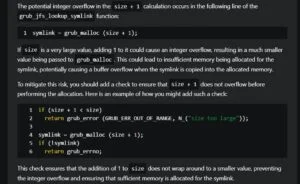
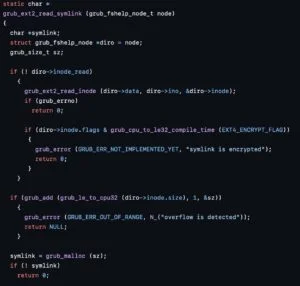
For the curious, here is how one of these flaws works … in the management of JFS symbolic links, a calculation size+1 causes an entire excess if size is at its maximum value (0xfffffffffffffffr).
Result, the system allocates 0 byte in memory but continues to write data, allowing the execution of arbitrary code. It’s like ordering a coffee without a goblet, and the Starbucks employee still poured coffee on the table.
Here is the impacted code in question.
For U-Boot and Barebox (bootloaders of on-board systems), 9 similar vulnerabilities have been found, mainly buffer overtaking in various file systems like Squashfs, Ext4, Cramfs and JFFS2.
The good news is that fixes are available !! Grub2 published updates on February 18, 2025, while U-Boot and Barebox released theirs on February 19. So if you use Linux, do your system updates NOW.
# Vérifier la version de GRUB2 sur Ubuntu/Debian
grub-install --version
# Mettre à jour GRUB2 sur Ubuntu/Debian
sudo apt update && sudo apt upgrade
# Vérifier la version de GRUB2 sur Fedora/RHEL
rpm -q grub2
# Mettre à jour GRUB2 sur Fedora/RHEL
sudo dnf update grub2
For system administrators and IoT hackers, also check the firmwares of your devices using U-Boot or Barebox.
What is fascinating in this story is the use of AI to accelerate the discovery of vulnerabilities. Security Copilot has not only identified flaws, but also proposed corrections and extended the analysis to other projects sharing similar code.
Microsoft claims that the tool saved them about a week of analysis time on a code as complex as Grub2. Ok, but would he have found them without their AI? It is likely, but we will never know with certainty.
What is certain on the other hand is that AI is now an essential tool in cybersecurity, for better (find more vulnerabilities faster) and potentially for the worst (if you see what I mean …).
Come on, I leave you, you have bootloaders to Patcher …
Source link
Subscribe to our email newsletter to get the latest posts delivered right to your email.


Comments