Configuring an email server is really a good thing. Especially since today it is no longer done as in 1997 & mldr; It has evolved well with new concepts related to security such as SPF, DKIM or DMARC. And without these protections, it is open bar for criminals who can send emails by pretending to be you. Flipping, right?
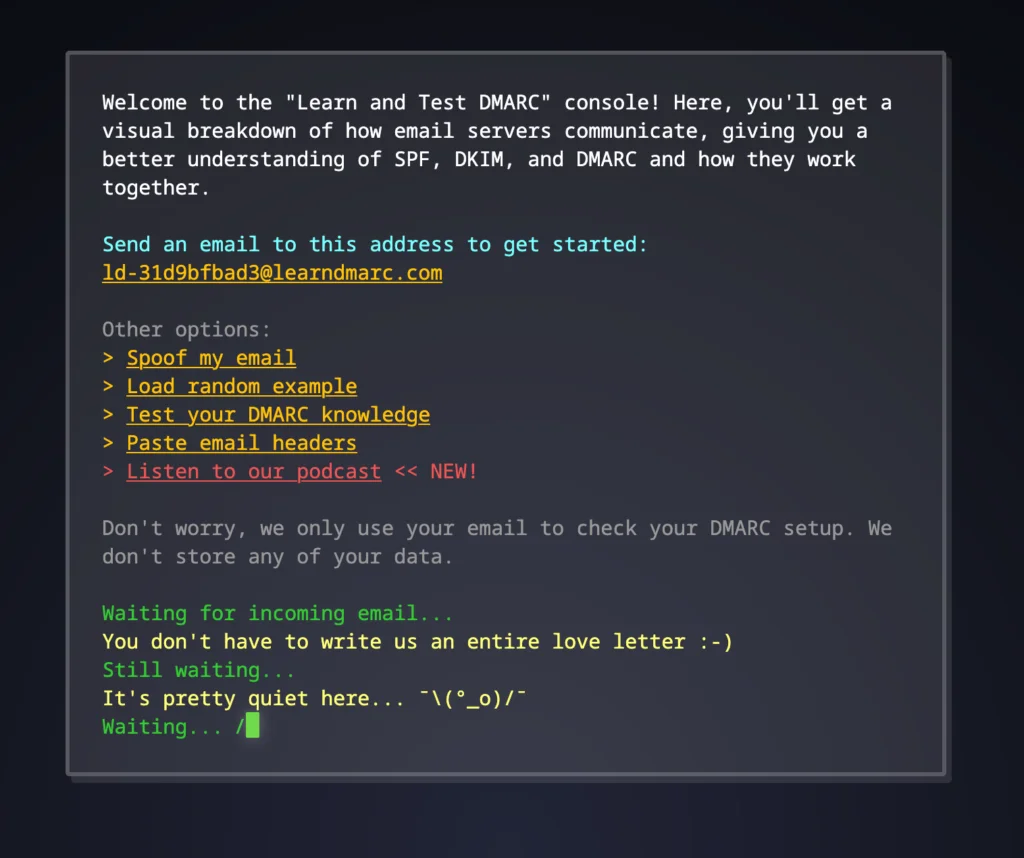
Personally, for a long time I did not understand much until I discovered Learndmarc. This site, created 3 months ago, is a small nugget that allows you to visualize and understand how these email safety protocols really work. The interface is intuitive and shows in real time how servers communicate when you send a message.
The really cool part is that you can test if your field is well protected by simply sending an email to their test address. In a few seconds, you will know if your configuration holds up or if it is a phishing colander.
But what exactly is SPF, DKIM and DMARC?
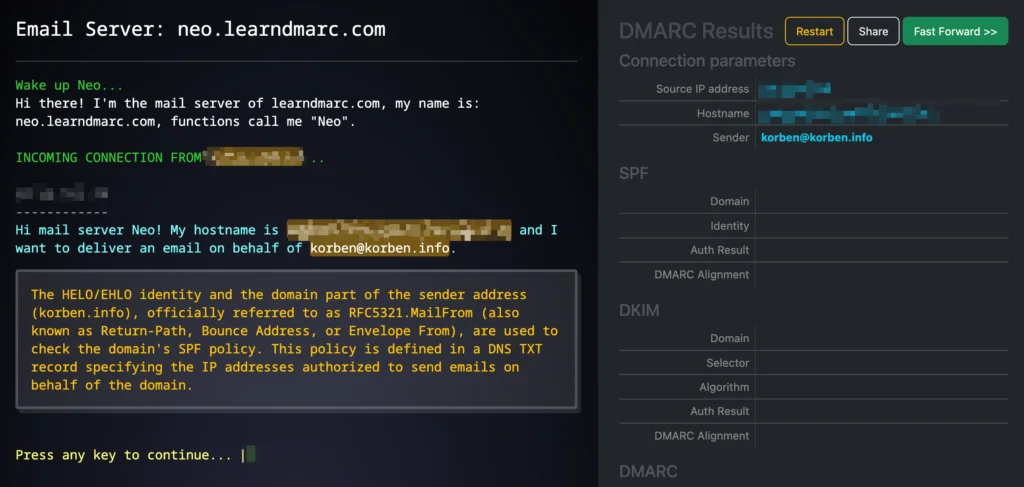
Basically, SPF is like the list of guests at the entrance to a VIP & MLDR evening; It defines which servers have the right to send emails for your field. Dkim is a cryptographic signature that proves that the message was not falsified in transit, a bit like the UV stamp on your hand at the entrance to the club. And Dmarc? Well it is the head of security who decides if we let pass, if we quarantine, or if we completely reject suspicious emails.
Without these three email safety musketeers, anyone can pretend to you and send emails on your behalf. So imagine the consequences for a moment if someone sent dubious messages to your customers by pretending to be your business & mldr;
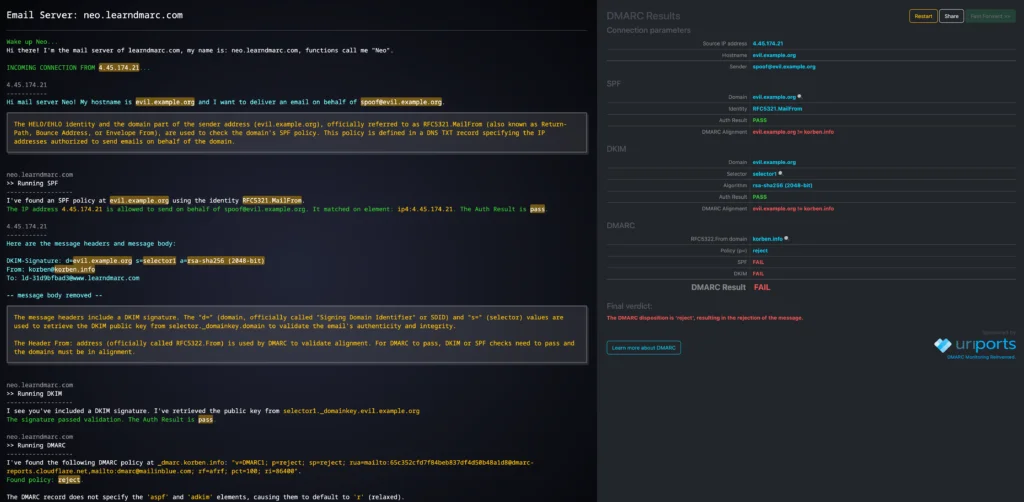
Learndmarc also has a really cool “spoof my email” feature. It allows you to simulate what would happen if someone tried to usurp your field to send fraudulent emails. No need for third -party tools or advanced skills & mldr; In a few clicks, you will know if your emails would be rejected, quarantined or worse & mldr; accepted without problem by the recipients.
The popularity of the tool has also exploded: more than 76,000 unique visitors in a few days after being mentioned on Hackernews. And all this for free, without storing your data. It’s rare to find such useful tools!
So how to test your domain in 30 seconds?
1. Send an email from your address that given by Leandmarc
2. Wait a few seconds for the analysis to appear
3. And after, click on “Spoof my email”
4. Enter your domain and see if it is vulnerable
If you discover that your field is vulnerable (result in red), do not panic. The implementation of these protections is not so complex, even if it scares at first. It’s like configuring a router, it’s intimidating at first but logical once you understand the basics.
Here, now you have no more excuses to get started. The interactive side is really cool and allows you to anchor all these concepts in our brain by using them. In an hour, I learned more about email security than to read technical documentation.
So, is your field well protected? Take the test !!
A big thank you to Letsar For discovery!
Source link
Subscribe to our email newsletter to get the latest posts delivered right to your email.


Comments