Do you know this new joke about Google engineers?
Well they invented a new type of encryption “end-to-end” (from start to finish), except that it is not really “end-to-end”. Welcome to the wonderful world of tech marketing, where words have the same meaning as in the dictionary.
This is how today, Google gives us a “revolution” for the encryption of emails in Gmail which is not an April Fool and which deserves that we look more closely & MLDR;
And yes because many companies have entrusted all of their messaging to Google & Mldr; As Admin Sys, imagine having to explain to your CEO why the email containing the acquisition strategy at 10 million euros leaked to your competitors & MLDR; Not very fun as a situation, suddenly, this encryption in Gmail is rather a good idea, right?
First, let’s start with a little accelerated history lesson. Email encryption has existed since digital prehistory & mldr; PGP was created in 1991S/mime appeared in 1995, that is to say again at the time when we connected with modems at 56k Biiip Shhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhhumenk Krlrkrkrk & mldr;. And here we have been 30 years later, with emails that is as popular as Windows Vista.
For what ? Well had to vote Macron. Uh, no, that’s not it. It is because it is a monumental gas factory good god !!! According to a Google study, less than 5% of professional emails are currently encrypted. Here is the cat! Especially since configuring S/Mime, it is like putting on a Conforama furniture without notice, hands tied in the back and blindfolded. It is easier than with the instructions but it is boring.
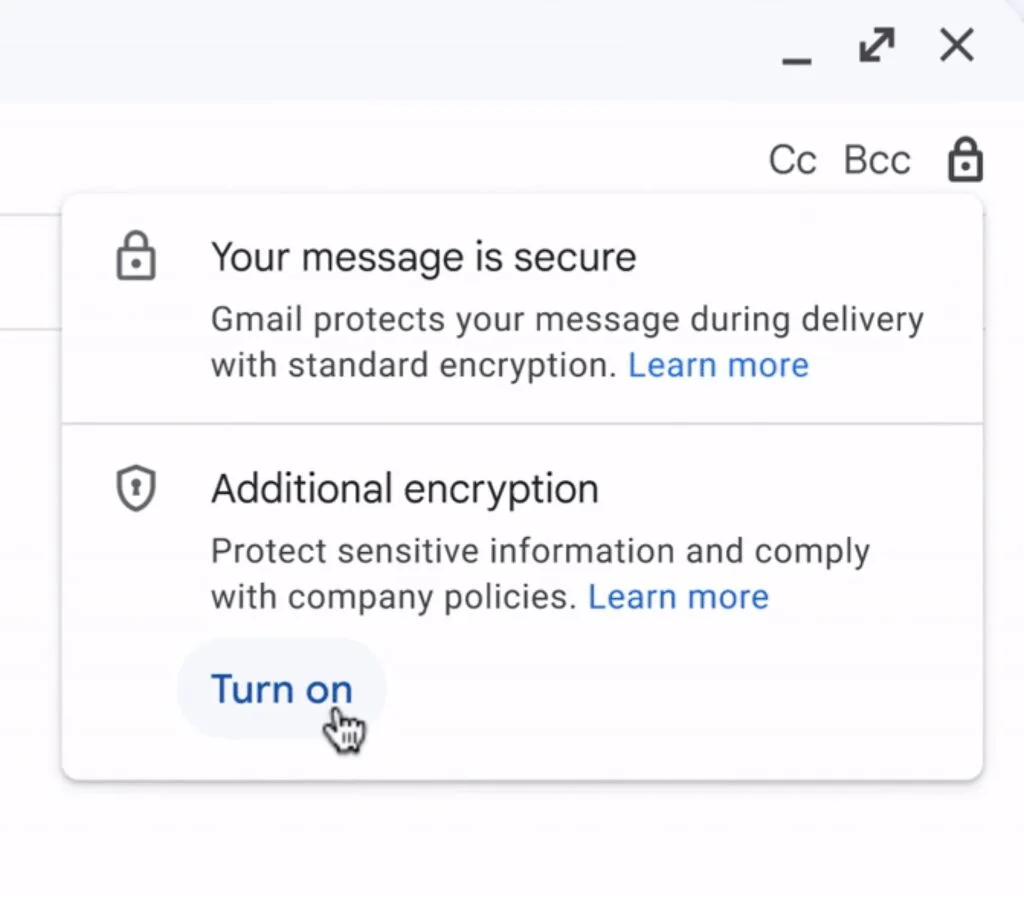
Google therefore decided to tackle this problem with its new Amazing approach !! No more complexity, hello simplicity: a simple button “Additional Encryption”In the email composition interface and hop, your email is encrypted.
And for recipients who also use Gmail, it’s transparent: they directly receive the message with a nice blue banner indicating “New Encrypted Message”. And for others (users of Outlook, Yahoo or others), they receive a link allowing them to access a limited version of Gmail where they can read and respond to the message after being authenticated. Basically, it is Google who says to them:“Come to my secure living room to read this message, it’s Cozy and warm but wipe your feet before entering.»
The deployment has already started, first in beta for emails within the same organization, then for all Gmail users, and finally for all mailboxes. So, by the end of the year, anyone can send encrypted emails to anyone. It is therefore a real democratization of encryption, and that’s super cool !!
End of the article ??? Naaaaan! Wait a minute, a bunch of impatient! Because when we look under the hood, we realize that Google plays “a little” with the words. They call it “End-to-end Encryption”(E2ee), but security purists are screaming in scandal (and not“ screaming with sandals ”is not yet the holidays). In reality, what Google has been in place is called“Customer-Side Encryption”(CSE). The difference is not just semantic, it is fundamental!
In a real E2EE system as a signal or WhatsApp, encryption keys are generated and remain only on end user devices. No one else, not even the service provider, can decipher messages. It is the Holy Grail of Communications Safety and that is why the States want backdoor in all these services!
But with Google’s CSE, The keys are generated and stored in a Cloud Key Management Service. Administrators can therefore access it, revoke access, monitor what users estimate. So it’s a kind of an ultra-secure safe protecting your most sensitive data, but where the guy who installed it has kept a double of the key “In case”, and could even look at what you store in it if it gets bored.
You will understand, this nuance has important practical implications. First, the system requires an external keys management service (not managed by Google). For this, Google has established partnerships with several suppliers, but it represents an additional cost. Then the administrators have a total control & mldr; They can see who, what, revoke access, define policies. And to perfect imperfection at all, some Google features are not available with activated CSE. For example, everything that is intelligent suggestions, the analysis of attachments, and certain research functions are deactivated. In addition, the encrypted content is not analyzed to detect phishing or malware when they have the keys & mldr; Too bad, it makes an additional potential flaw in your safety.
So, for whom is this solution really designed in the end? Well without surprise, it is a solution designed for companies, not really for the small paranos that we are. For companies, it is clear that it is a small revolution. Administrative control over encrypted communications is total. We can revoke access to certain content, apply compliance policies, and all without the Kafkai complexity of S/Mime. On the other hand, you must have the well -filled pockets because the functionality requires Google Workspace Enterprise Plus ($ 25 per user and per month), Standard Education or Education Plus.
Besides, Microsoft has been offering the same thing since January 2025 with Purview Message Encryption for M365 E5 customers (what name in the idiot!) For $ 38 per user and per month. The Microsoft solution works almost identically with transparent encryption between Outlook users and secure links for users of other platforms. In short, the race for encryption-pass-chifframent is launched between the giants.
For IT administrators, this is paradise. Simplified configuration, possibility of monitoring what users estimate, options to define CSE as default parameter & mldr; They can even use smart cards for hardware key encryption in Gmail if the organization has particularly high safety needs.
And for end users, it is the embodied simplicity & mldr; A simple button and that’s it, it’s encrypted. They can send to anyone, even without technical knowledge.
In short, it’s cool for pro but for the purists of privacy, it is the big disappointment. As it is not real E2EE and administrative control implies confidence in the organization that manages the boxes, it is better to orient yourself on protonmail (from € 8 per month) or tutanota, which remain options of choice.
There are also some gray areas to consider in this implementation of encryption made in Google & Mldr; For example, the link sent to non-gmail users to access encrypted messages is furiously like the Docs/Sheets invitations. The kind of thing to make the happiness of phishers that were just waiting for that. Google of course integrated warnings to reduce this risk, but which really reads these warnings?
Also ask questions of data sovereignty. Who really controls your data if you depend on an external keys management service? For organizations subject to regulations like the GDPR, this is a question that deserves reflection.
Finally, the accessibility of encrypted content also poses a problem for research and archiving, but that’s a classic problem of this kind of implementation. As such, Google Vault makes it possible to keep and export these emails, but you need a specific utility (the “decrypter”) to decipher them. Practical, but not really transparent for used users to be able to search for any content in a few clicks.
In the end Google ended up an attractive compromise between safety and usability, but no, it is not the perfect E2EE that Cyphenpunks have been waiting for 30 years. So yes, it will make the purists scream but for the first time, we have a solution that could finally democratize the encrypted email beyond the usual tech circles.
Source link
Subscribe to our email newsletter to get the latest posts delivered right to your email.


Comments